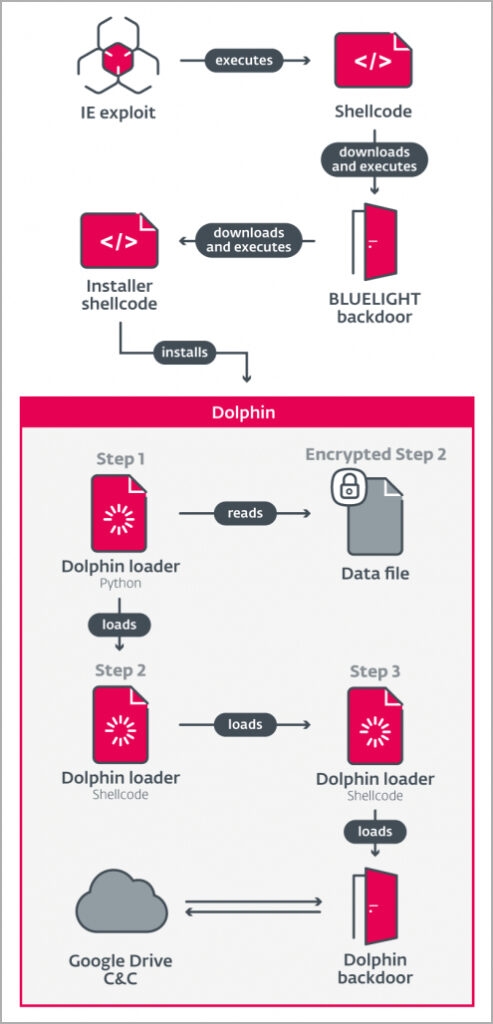
The APT 37 group Reaper, Red, Eyes, Erebus, & Scarcruft has used the Dolphin malware against very specified entities. This group has been linked with spying activities associated with North Korean interests since 2012. The malware, i.e., Dophin, was first detected by ESET researchers in 2021, and since then, it has evolved into new variants with improved codes and anti-detection methods. Well, the attackers do not use Dolphin alone; BLUELIGHT is used along with the Dolphin. BLUELIGHT is a basic espionage tool that has been a part of previous AP37 campaigns though it has more powerful abilities, i.e., stealing passwords from web browsers, logging keystrokes, and taking screenshots. The BLUELIGHT is used to start the Dolphin Python loader on an infected computer though it has a very limited part in spying activities The Dolphin Python loader, which includes a script and a shellcode, launches a multi-step XOR decryption creation which, in the end, results in the Dolphin payload in the newly created memory process. Well, the malware Dolphin is a C++ executable that uses Google Drive as a command core C2 server to keep stolen files, and the malware begins persistence by altering the Windows Registry. Read: Fake MSI Afterburner Portal Targets Windows Gamers for Mining Crypto The malware at the initial stages collects the following information from the compromised computer.
Username Computer name Local and External IP addresses Installed Antivirus RAM size and usage Existence of debugging or network inspecting tool Operating System version
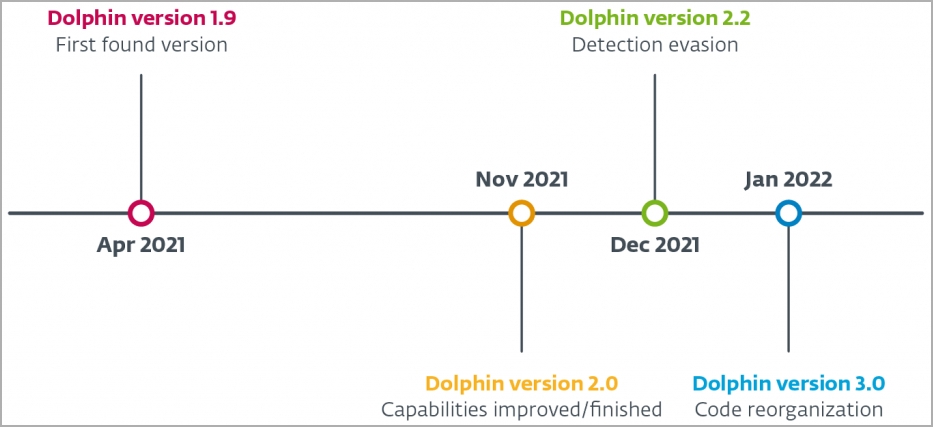
Furthermore, the malware also the C2 server its current configuration, time, and version number, and the configuration hold keyloggers and also data exfiltration instruction and login details for Google Drive API, encryption keys, and access. According to the ESET researchers, the attackers sent their commands to the malware by uploading them to Google Drive, and in return, the backdoor, i.e., Dolphin, uploads the results from executing those commands. In addition, the Dolphin has an increased set of capabilities that includes scanning local & removable hard drives for a variety of data like images, documents, certificates, and emails. The feature was then improved further to filtrate data by extension. The malware has an increased search capability via which it can scan any phone which is connected to the infected computer by using the Windows Portable Drive API. However, the researchers at ESET say that this function was still being developed in the first version of the malware that they discovered! Examples of it are as follows. Use of a hardcode path with a username that likely does not exist on the victim’s computer. Missing variable initialization – some of the variables are assumed to be zero-initialized, or they are dereferenced as pointers without initialization. Missing extension filtration. Moreover, it can also weaken the security of the victim’s Google account by changing its related settings of it, and in return, this allows hackers to have access to the Gmail account for a longer time. Also, the malware can note down the keystrokes by exploiting Google Chrome GetAsyncKeyStateAPI. It can take a screengrab of the active window every 30 seconds. The researchers at ESET security firm have already found four different variants of the Dolphin malware since January 2022, and it is possible that the newer version of Dolphin exists and possibly has been used in attacks already because the backdoor has been used against specific targets. ESET researchers added that the Dolphin malware was used in a water-hole attack on a South Korean newspaper reporting on activity and events related to North Korea. The hackers used Internet explorer to deploy the Dolphin malware to target the hosts. Read: Google Pushes Chrome Update to Fix its 8th Zero-day Vulnerability of the Year