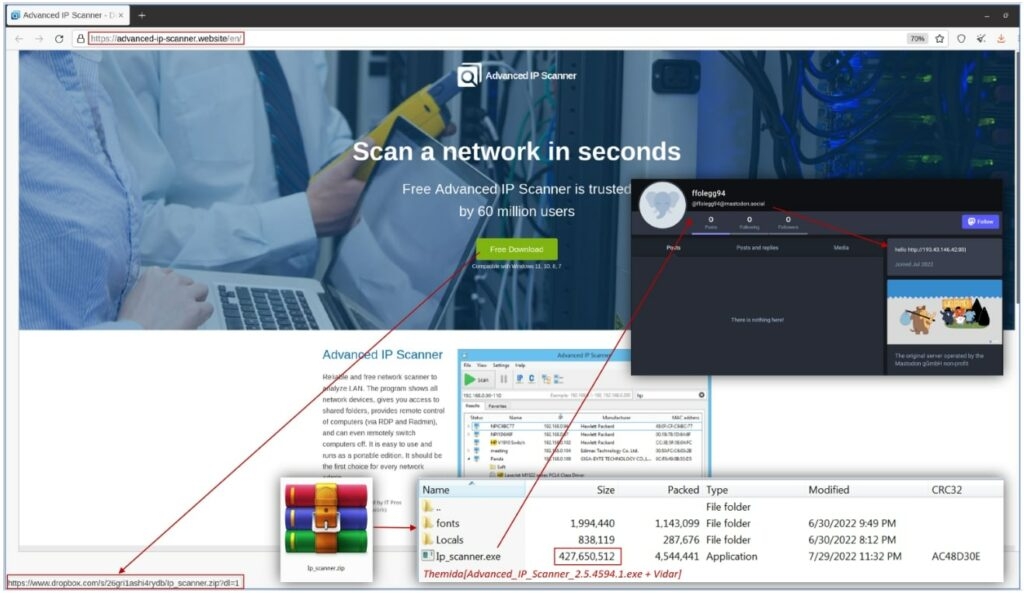
The Computer Emergency Response Team of Ukraine (CERT-UA) – which functions as part of the State Service for Special Communication and Protection of Ukraine, confirmed the outbreak via their portal. The CERT-UA mentioned that the attacks were from ‘Russia with Love (FRwl). Or Z-Gen (Which the CERT-UA keeps an eye on as UA-0118). The hacktivist group had earlier revealed the Somnia ransomware on Telegram & posted the attacks that they carried out on tank producers in Ukraine. With that being said, Ukraine till now has not confirmed any successful encryption attempts by Russia with Love hacktivist group. Now, as per the Computer Emergency Response Team of Ukraine, the group uses fake websites that copy the Advance IP Scanner software to fool Ukraine’s organization employees into downloading an installer. The fact that installer infects the system with the Vidar Stealer, which in turn then steals the victim’s telegram and takes control of the account. Also, the CERT-UA mentioned that somehow in an unidentified manner, the hacktivist group exploited the telegram account of the victim to steal the VPN connection data. Well, if the VPN is not secured by the 2-factor authentication, then the group can use it to get unauthorized access to the victim’s corporate employer network. The hacker injects a Cobalt Strike beacon, exfiltrates data, and then uses Rclone, Anydesk & Ngrok to execute various surveillance & remote access activities Furthermore, the CERT-UA said that since the spring of 2022, this Russian hacktivist Zgen group has carried out several attacks with the help of initial access brokers on Ukraine’s organizations. Moreover, the latest samples of the ransomware, i.e., Samnia, suggest that the attacks depend only on the AES algorithms. Although, in the beginning, Somnia ransomware used 3DES. These are the file types targeted by Somnia, including images, documents, video, archives, databases, and more, which reflect the damage they are trying to achieve with this ransomware. Somnia ransomware attaches .somnia extension to the encrypted files name when it is encrypting those files. Well, unlike the usual Ransomeware attack, which asks the victim to pay money in exchange for the decryptor. However, the Somnia ransomware is more interested in disturbing the target operations than generating revenue. Hence the Somnia ransomware is considered a data wiper attack rather than a conventional ransomware attack.